The Human Element – Everything you should know about Social engineering vulnerabilities

Social engineering – Two innocuous words that could independently mean something absolutely different, yet when put together take you into a sinister sphere of deception. In the world of cybersecurity, social engineering refers to the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.
It is essentially the art of manipulating people, so they give up confidential information. The types of information these cyber criminals are seeking can vary, but when innocent people are targeted, they are usually tricked into giving up their banking and other financial information, passwords or coaxed into installing software that can get these details for them.
Remember how we said social engineering is an ‘art’, that is because while it is done with scientific methods and using technology much of the deception is still planned out and implemented using old time ways to deceive people, playing with emotions.
Talk to any good security professional and they will tell you that the weakest bond in the security chain is the human being who accepts a person or scenario at face value. Even if there are burglar alarms installed, locks at the door, fences and just about every security measure installed there can still be a risk if there is a person opens the door to someone they don’t know or haven’t checked to see who is outside.
What this could essentially mean is that the human element is the most important when it comes to cybersecurity, especially when it comes to preventing and detecting social engineering especially since there are many ways scammers could run social engineering schemes.
[optin-monster-shortcode id=”dv4jqlr9fih8giagcylw”]
According to security experts, only about 3 percent of the malware they run into tries to exploit a technical flaw. The other 97 percent tries to trick a user through some type of social engineering scheme. Hackers understand that social engineering is much more efficient than trying to find technical flaws and use them to their advantage. It is time security experts understood this too.
According to the U.S. government’s National Cyber Awareness System, critical infrastructure is targeted by using Spear-phishing emails, Watering-hole domains, Credential gathering, Open-source and network reconnaissance and also Host-based exploitation
Spear phishing is personalized for the people intended and is the fraudulent practice of sending emails from a known or trusted sender in order to induce targeted individuals to reveal confidential information. Because of its personalized nature, spear-phishing emails represent the largest threat for nuclear plant operators.
However, according to experts, phishing scam concerns have been consistently rated lower compared with other OT/ICS threats, yet there continues to be evidence from ICS attack research that this tactic is still a favored mechanism to establish an initial point of compromise and entry into many industrial control systems in the OT domain. Experts have also stated that decrease in concern around phishing scams may lead to misplaced investments that leave OT even more susceptible in the future to phishing campaigns.
According to Chad Lloyd, a security architect and Senior Edison Fellow with Schneider Electric, Social engineering relies heavily on the 6 principles of influence. These include – Reciprocity, Commitment and consistency, Social proof, Authority, Liking and Scarcity.
 “Exploitation and execution really go hand and hand. Exploitation is getting your foot in the door. Those drop and a phishing email and see if they’ll click, where the execution on the other hand is the payload that’s hidden within phishing email. Now, in addition to traditional social engineering techniques, one of the things that are critical, infrastructure facilities are really getting hit hard with right now is called the advanced persistent threat. The advanced persistent threat is a targeted attack on generally a specific individual that holds crown jewels or potentially holds the ability to control specific systems within your facility,” Lloyd said.
“Exploitation and execution really go hand and hand. Exploitation is getting your foot in the door. Those drop and a phishing email and see if they’ll click, where the execution on the other hand is the payload that’s hidden within phishing email. Now, in addition to traditional social engineering techniques, one of the things that are critical, infrastructure facilities are really getting hit hard with right now is called the advanced persistent threat. The advanced persistent threat is a targeted attack on generally a specific individual that holds crown jewels or potentially holds the ability to control specific systems within your facility,” Lloyd said.
Examples of going through recognizance with advanced persistent threat (APT) could be that they may try to befriend you in person. They may go through your social networks and find things that you’re interested. The exploitation and execution are going to be fairly similar to a normal social engineering attack, except they’re going to a direct application. It could also be a lot more personalized than a regular spear phishing attempt.
Scammers who are social engineering experts are also good at psychology. There are some interesting terms from that sphere that you may encounter if you start researching social engineering. The first is reciprocity.
“Reciprocity at its very basic level is that if I do you a favor, you’re more likely to do me a favor and sometimes it is quid pro quo. The other really interesting thing about reciprocity is that if I can get you to do me a favor, you’re more likely to do me another favor,” According to Chad Lloyd.
Employed at Schneider Electric since 2007, Chad Lloyd is a member of the Schneider Cyber Security Team and is involved with software and solution design and development. In addition to duties within Schneider Electric, Chad was also an adjunct professor at Middle Tennessee State University teaching Local Area Networks with an emphasis on network security.
He brings up various psychology concepts while talking about social engineering. Another one mentioned was Cognitive context and framing. Framing is all about ‘the here and now’, also known as cognitive context.
In psychology, the framing effect is a cognitive bias where people decide on options based on whether the options are presented with positive or negative connotations; example as a loss or as a gain. People tend to avoid risk when a positive frame is presented but seek risks when a negative frame is presented.
Hackers and phishing experts tend to reach out to the cognitive bias of the person who is making the decision by presenting a scenario which could look like a positive one.
“You may also use this thing called the prospect theory. This is an interesting physiological theory, say you lose a $1000, you literally lost in the streets. If you were to find $1000, literally the next day, you still would feel bad about losing the $1000, does that make sense. Even though it’s the same amount of money, even though you are back to par, because you lost it, you can’t gain the same amount to feel better about it. Now, you double it and maybe you’ll feel better about, gain $2000. By using the prospect theory, you can bring your context or your pretext so that when you’re communicating with the victim you can say, if you don’t do this, you’re likely to lose this. In other words, the point is, if you can tell them there are going to lose something it’s much more effective than if you tell them they are going to gain something.”
Physiological theories suggest that responses within the body are responsible for emotions and the knowledge that hackers are using these theories to get unsuspecting victims fall for their manipulation is both impressive and scary.
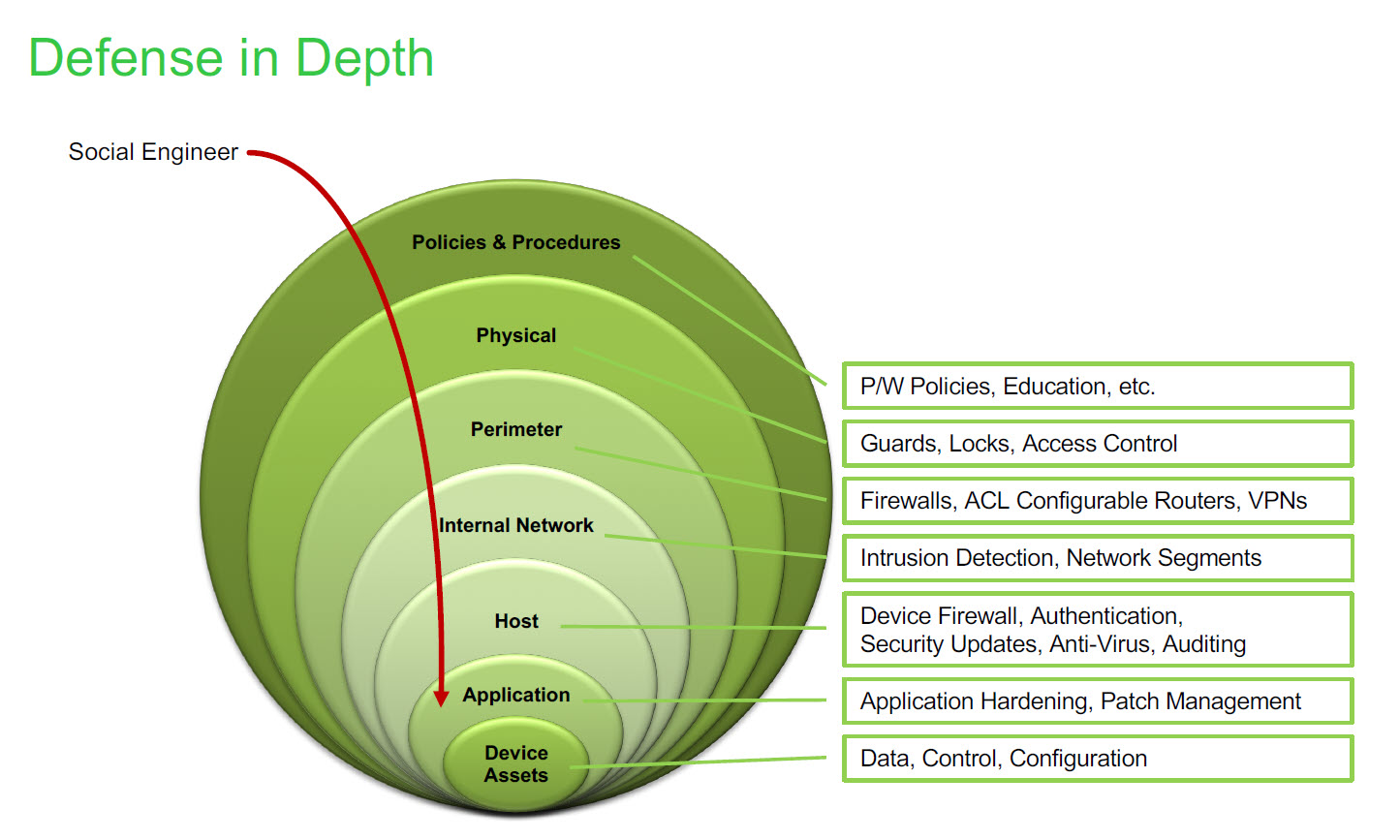
One fact that almost all experts both cyber security and traditional security experts agree with is that training still remains the best way to deal with the potential of new threats. The primary focus of security awareness programs should be social engineering and people with risky positions where high priority information can be compromised should be given special targeted training on identifying risk factors in social engineering circumstances. The training sessions should be short, interesting and interactive to make it easier for all the stakeholders involved.
Employees, who have access to privileged and sensitive data, should be given high priority training regularly and they should take it very seriously. Similarly, third party employees and vendors should also be provided with training and if they say they have training in cybersecurity and social engineering then doing some testing could be a great way to keep them on track while also making sure they are trained.