Secure remote access in the COVID-19 Era
In January, Forrester Research released a study looking at how the expanded remote workforce is impacting security and how organizations are adapting to secure themselves in the post-COVID Era. The study found a link between the rise in remote work and security risk, demonstrating the need for secure remote access.
“The COVID-19 pandemic necessitated a massive and immediate move to remote work, accelerating a shift that was already in motion but previously happened with more foresight and planning,” the report says. “This accelerated shift has made organizations increasingly vulnerable with now larger-than-ever attack surfaces. Traditional privileged users (IT admins and others with powerful access to IT systems) are now working remotely, and traditional business users are requiring privileged access to perform their jobs from home. Corporate endpoints have moved to workers’ homes, quickening the trend toward “identity as the new perimeter” and accelerating the adoption of zero trust approaches. Simultaneously, companies have expedited digital transformation initiatives, such as the shift to cloud, which is further disintegrating the traditional perimeter.”
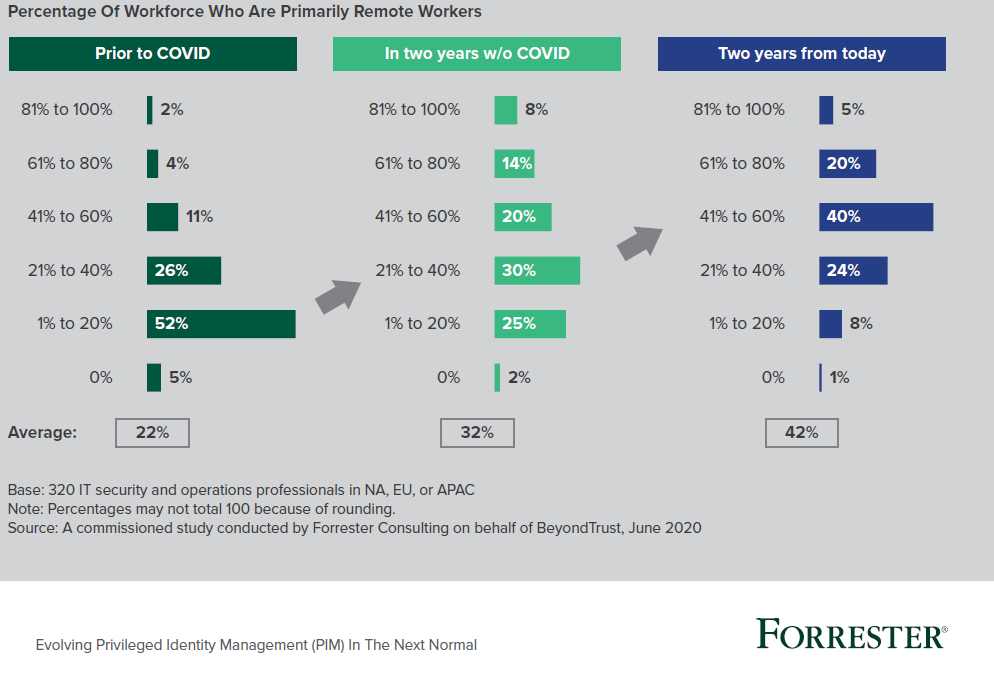
Percentage of Workforce Who Are Primarily Remote Workers
The Forrester study was commissioned by privileged access management provider BeyondTrust to evaluate the challenges facing privileged identity management during the pandemic. It includes a survey of 320 IT and security decision makers in North America, Europe, and Asia.
According to the report, 83 percent of survey respondents report the rise in remote workers increases the risk of a security incident. Additionally, the study indicates the remote workforce is increasing the need for privileged access, which has increased the importance of privileged identity management to security leaders.
“Security leaders must navigate these unprecedented and uncertain waters by rapidly changing, augmenting, and adapting their security systems to keep their organizations protected from threats, the report says. “Relying on perimeter-based network security and legacy remote technologies like VPN for remote access does not provide the granular identity-based security that is needed when the workforce — and the apps, data, and infrastructure they are using — could be located anywhere. Privileged users also require additional access controls that still allow them to do their jobs and keep the entire remote workforce productive. Security leaders must rethink their privileged identity management (PIM) strategies to go beyond traditional password management and embrace the full spectrum of PIM, including endpoint privilege management and secure remote access.”
In the survey, 91 percent of respondents agreed that PIM plays a crucial role in securing remote workers. Eighty-six percent of respondents say their organizations will invest more in PIM over the next two years to address the risks related to remote work. And, 56 percent report that improved IT administration efficiencies are the top benefit of PIM .

Morey Haber, CTO and CISO at BeyondTrust
“The findings of this global survey confirm the fact that the pandemic has accelerated the borderless enterprise and brings identity to the forefront of the new perimeter,” Morey Haber, CTO and CISO at BeyondTrust, said in a press release. “To protect their assets, enterprises must secure their data throughout their IT estate. This requires comprehensive PIM solutions that enable uncompromised access to applications and data from anywhere, by any user or device.”
Industrial Cyber talked to BeyondTrust’s CISO and CTO about remote access and the increasing risk facing industrial environments.
“Industrial Control System (ICS) environments exist to provide robotic and automation support for manufacturing, critical infrastructure, and a wide variety of implementations that are highly dependent on environmental factors such as timing, temperature, pressure, speed, and other qualitative metrics,” Haber says. “If any set of critical values changes, ICS environments are designed to alter settings in other systems to modify the workflow or in the worst-case scenarios, perform an automated shutdown. If these boundary conditions are not properly observed, catastrophic failures can occur and can affect production or even impact human lives.”
Industrial control systems are usually maintained in closed or air gapped environments in order to ensure no external factors can cause a disruption in monitoring, operations, or runtime.
“However, like any computing system, ICS environments can have vulnerabilities and will need periodic maintenance for upgrades, faults, and basic monitoring,” says Haber. “Any downtime does represent a cost to the ICS environment that needs to be considered. The question, therefore, becomes how to provide secure remote access to administrators and engineers without compromising the integrity of the closed network and ensure malicious network traffic cannot penetrate the environment during a remote access session or during normal operations?”
According to Haber, proxy or gated based remote access provides a single point of connectivity to all devices in the ICS environment using a bastion host for session management. It can perform remote access using a variety of protocols with, or without agents, using native standard protocols (RDP, SSH, VNC), web browsers (HTTP, HTTPS), and even fat clients operating over proprietary protocols to provide connectivity.
“Remote access sessions, and accompanying network traffic, need to be ephemeral and remote access only permitted when just in time requirements have been met,” Haber says. “In addition, remote access should be point-to-point to avoid exploitation of any vulnerabilities associated with other devices and not use native operating system or application protocols for access to avoid a similar type of exploitation on the target system,” Haber says. “Therefore, proxy or gated based remote access is the best security solution for managing remote access into ICS environments.”
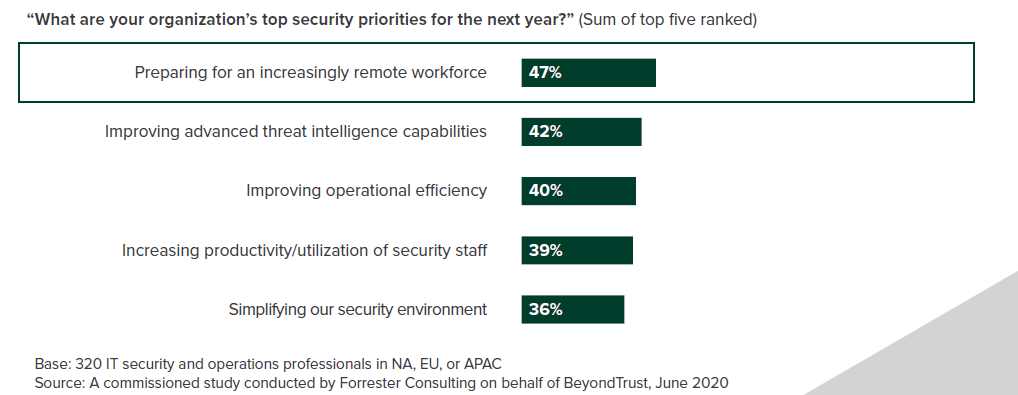
“What are your organization’s top security priorities for the next year?”
Haber says that proxy or gated based remote access allows users to perform session monitoring and recording for training and to demonstrate the access was appropriate and compliant. It also provides privileged credential injection into the session in order to avoid disclosure of privileged accounts outside of the ICS enclave. Additionally, this kind of remote access does not require network layer routing technology like VPN to provide a secure remote access session.
BeyondTrust’s report recommends organizations plan for the rising tide of remote privileged users and implement strategies to reduce the attack surface and prevent lateral movement. Additionally, organizations should apply just-in-time access approaches for dynamic business use cases, balance UX with security controls for remote privileged users, and provide centralized, consistent administration with an integrated PIM suite.
“The seismic shift to remote work, brought on by COVID-19, has accelerated the trend toward zero trust and identity as the new perimeter,” the report says. “Remote work will drive up the number of privileged users and privileged sessions over the next two years. Privileged users are critical to the operations of digital business, yet as power users, they also present a grave security risk to organizations. Firms must put effective PIM controls in place to limit the attack surface while still enabling regular business operations.”









